Preparing Domain Group Policy Settings for Windows Miracast over Wi-Fi Direct
Preparing Domain Group Policy Settings for Windows Miracast over Wi-Fi Direct
This article applies to ScreenBeam 1xxx-Series, 960, and 750 products.
ScreenBeam Wi-Fi Miracast operates in Autonomous Group Owner (AGO) mode by default. This approach allows organizations to specify a wireless channel(s) for the Wi-Fi Direct peer-to-peer connection.
In this mode, the P2P connection may be prevented by the domain Group Policy. If a domain-joined Windows Miracast connection attempts fail repeatedly and show the "Couldn't connect" message on the PC, you may need to configure the Microsoft Active Directory Group Policy setting for wireless display.

Under Group Policy Management Editor > Policies > Windows Settings > Wireless Network (IEEE 802.11) Policies
Windows 10/11 client systems
-
Uncheck Prevent connections to infrastructure networks
-
Check Allow everyone to create all user profiles
-
Uncheck Don't allow Wi-Fi Direct groups
Windows 7 client systems
-
All settings mentioned above
-
Uncheck Don't allow hosted networks
Settings highlighted in green are required for all versions of Windows, settings highlighted in blue are only required for Windows 7.
Make sure the new group policy setting is applied to the client systems by opening an administrator command prompt and entering gpupdate /force.

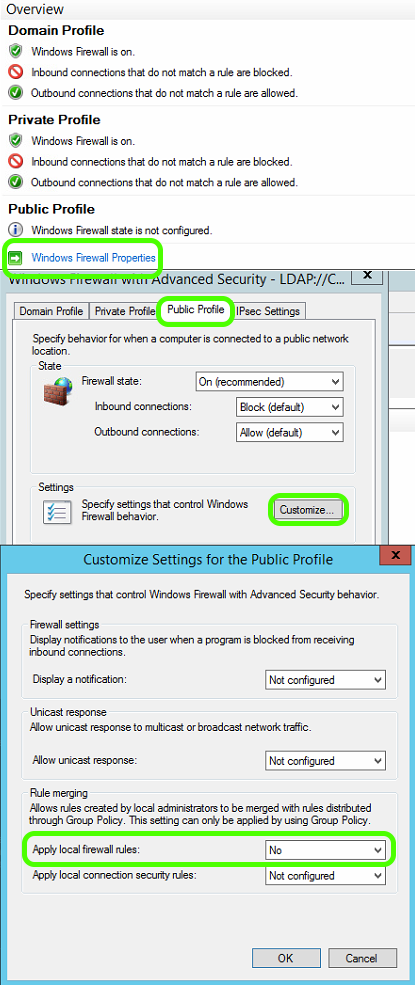
Under Group Policy Management Editor > Policies > Windows Settings > Security Settings > Windows Defender Firewall with Advanced Security
If the Windows Defender Firewall is enabled through Group Policy and under Windows Firewall Properties for the Public profile, and if the settings have been Customized such that Apply Local Firewall rules are set to No then Domain PCs will not be able to connect to the ScreenBeam unless a firewall exception is created at the Group Policy level.
Peer-to-peer Miracast always uses the Public Profile.
The simplest method is to create a Firewall rule in Group Policy to allow all ports/protocols/Public Profile for %systemroot%\system32\WUDFHost.exe
If using Miracast over LAN
Only applicable to ScreenBeam 1xxx-Series and 960. Additional Group Policy rule that must be considered.
Under Group Policy Management Editor > Policies > Administrative Templates > Network > DNS Client
Turn off multicast name resolution must be set to Disabled or Not Configured. Miracast over Infrastructure is not compatible with multicast name resolution Enabled.
